The UK Research Institute in Secure Hardware and Embedded Systems (RISE) 3rd Annual Conference was held on 30th November 2020.
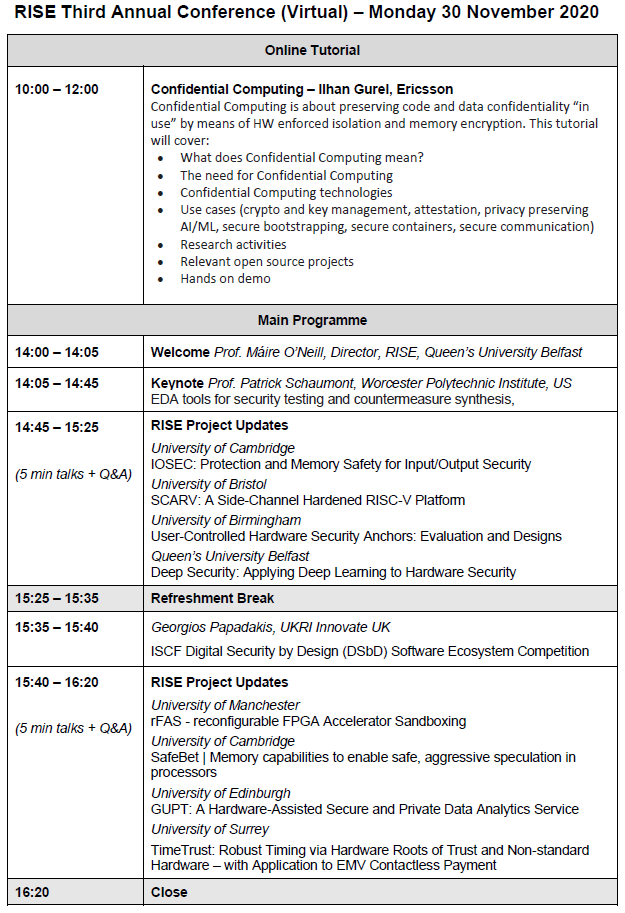
Tutorial Session
Confidential Computing is about preserving code and data confidentiality “in use” by means of HW enforced isolation and memory encryption.
This tutorial will cover:
• What does Confidential Computing mean?
• The need for Confidential Computing
• Confidential Computing technologies
• Use cases (crypto and key management, attestation, privacy preserving AI/ML, secure bootstrapping, secure containers, secure communication)
• Research activities
• Relevant open source projects
• Hands on demo
Bio: Ilhan Gurel works for Ericsson in the CTO organization as an expert on trusted HW and SW technologies. Ilhan Gurel lives in Finland. His current role involves various security activities related to HW security, SW security, TEE (Trusted Execution Environment) technologies and practical use of cryptography.
Main Session
We are pleased to welcome Prof. Patrick Schaumont of WPI as our keynote speaker this year. The title of the talk will be EDA Tools for Side-channel Security Testing and Countermeasure Synthesis.
Abstract:
A crucial difference between hardware and software in computer systems is that hardware cannot be patched on the fly. With security vulnerabilities, it is especially important to make sure the hardware design gets it right-first-time.
In this talk, we focus on side-channel attacks, which use the physical byproduct of computing as a leakage source to break cryptosystems and other sensitive-computing forms. Because side-channel leakage is a physical phenomenon, it originates in hardware, even if the cryptosystem is implemented in software. Hence, we must understand the role of hardware in side-channel leakage. We will focus, in particular, on power consumption as a source of side-channel leakage.
By trade, hardware engineers optimize for maximum performance, minimal power consumption, or minimal cost. However, hardware designers are not used to handling side-channel leakage. We need novel techniques and tools to address side-channel leakage during hardware design, from its assessment to its mitigation.
We will review state of the art in design automation techniques to address side-channel leakage. We will show that design automation tools can model power-based side-channel leakage sources and predict side-channel attacks’ success rate. When the source of side-channel leakage is understood, design automation tools can also evaluate the impact and efficiency of side-channel leakage countermeasures, all of this without building and measuring physical prototypes.
Bio:
Patrick Schaumont is a Professor in Computer Engineering at WPI. He received the Ph.D. degree in Electrical Engineering from UCLA in 2004 and the MS degree in Computer Science from Ghent University in 1990. He was a staff researcher at IMEC, Belgium from 1992 to 2000. He was a graduate student and postdoc at UCLA from 2001 to 2005. He was a faculty member with Virginia Tech from 2005 to 2019. He joined WPI in 2020. He was a visiting researcher at the National Institute of Information and Telecommunications Technology (NICT), Japan in 2014. He was a visiting researcher at Laboratoire d’Informatique de Paris 6 in Paris, France in 2018. He is a Radboud Excellence Initiative Visiting Faculty with Radboud University, Netherlands from 2020. His research interests are in design and design methods of secure, efficient and real-time embedded computing systems. He served as program co-chair for several conferences in cryptographic and secure engineering, including CHES, HOST, ASHES, and FDTC. He received the National Science Foundation CAREER Award in 2007.
