
We are delighted to welcome another new guest blogger to contribute to the RISE blog for August 2019. Shichao Yu is a PhD student at Queen’s University Belfast, working in the world class research centre – The Centre for Secure Information Technology (CSIT). Thank you Shichao!
Welcome to Miami – Summer is coming!
Hi, I am Shichao, I am typing this blog shortly after the closing remarks of IEEE Computer Society Annual Symposium on VLSI in Miami, which is excellent and provided me an amazing conference experience. This was my first time in Miami, and this is the first conference I have attend with a poster paper. I travelled from Belfast to Miami, from north to south, feeling like I flew into the summer from winter when I just arrived there. If I choose rainy day as the mark of the climate in Belfast, then Miami’s symbol must be sunshine.
ISVLSI 2019 @ Miami
ISVLSI is an IEEE computer society annual symposium with a history over three decades. It explores emerging trends, novel ideas and basic concepts covering a broad range of VLSI-related topics, which also include new technologies and burgeoning application areas, such as hardware security, and artificial intelligence.
This year’s ISVLSI was held at Florida International University in Wolfe University Center.
What impressed me is that more than 25% of submissions this year related to system design and security (SDS), and the submission number occupies the first in all categories. I can see that the security direction is receiving increasing attention from researchers all over the world.
“Can you trust your machine learning system?”

For Hardware Security, the papers presented in this year’s security session mainly focused on logic obfuscation, side channel susceptibility mitigation, secure zone design on NoC (Network on Chip) and Hardware Trojan. The System Design and Security group covers four sub-sessions in three days and two related special session: “Botnet of Things: Hardware Insecurity in the IoT Era” and “Secure, Smart, Connected Devices for Emergent Applications”, which talk about IoT devices and it’s security problems.
In addition, an enlightening keynote “Can you trust your machine learning system?” presented by Professor Sandip Kundu on the second day really attracted me. This presentation showed the potential security issues of machine learning (ML) and deep learning (DL) at this stage and details the possible attack methods. As the Chinese idiom goes, virtue is one foot tall, the devil ten. It always takes constant vigilance to secure new technologies. (That scares me too Shichao!)
Poster Session

The poster session was held in the afternoon of the first day. We had a big ballroom to hang all 30 posters and 4 research demonstrations. The session last nearly two hours, which is much more than the scheduled time, with continuous technical discussions and social communication.
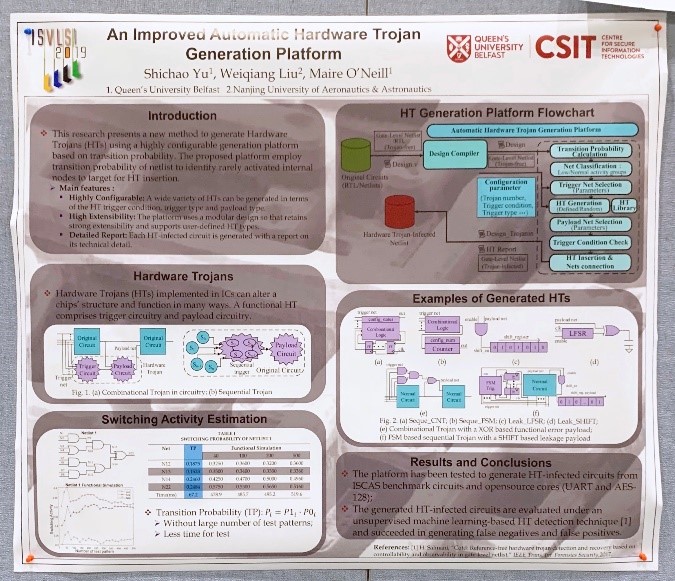
The paper I presented on my poster was “An Improved Automatic Hardware Trojan Generation Platform”, which is a new method to generate Hardware Trojans (HTs) using a highly configurable generation platform based on transition probability. (WOW :O – great stuff Shichao! \0/)
I always enjoy the discussion with other researchers. But, as I work in hardware security, I really hope that I had explained my poster clearly to some researchers who work in software side.
Until Next Time Miami 🙂
Three days ISVLSI went by too quickly and it was super busy. My record is slightly broken, but the great keynotes and presentations are unforgettable. Miami Beach is also beautiful and relaxing.
In the evening of the last day, I took a photo when blue hour made Miami Beach a little tranquil, and said goodbye to this beautiful city. (Good you got to check out the sandy beaches 🙂 BTW where is our present?? 😀 )

